Hackers demanded bitcoins from the state department of the Republic of Kazakhstan
JSC “State Technical Service” reports the detection of a network infection with an encryptor virus in one of the organizations of the quasi-public sector of Kazakhstan. To decrypt the attackers demanded a payment in bitcoins.
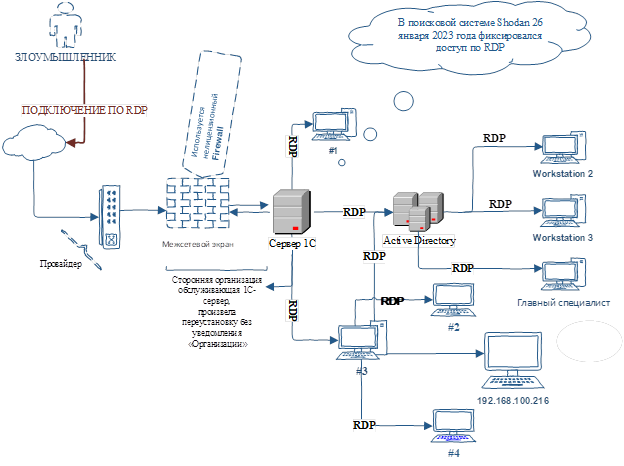
The preliminary analysis showed that the organization did not comply with the requirements of the Decree of the Government of the Republic of Kazakhstan dated December 20, 2016 No. 832 “On approval of uniform requirements in the field of information and communication technologies and information security” (hereinafter – UR). Thus, from the entire network of the organization, the attacker easily managed to infect a domain controller, three personal computers and a file server. Technical details of the information security incident investigation are here.
The specialists found that one of the personal computers was completely encrypted and the system logs were cleared.
For all users of the organization, only one account was created – “X”. Through password brute force using the RDP protocol (Microsoft’s Remote Desktop Protocol), the attacker gained access to the infrastructure and removed the anti-virus software on each workstation. After removing the antivirus software, the ransomware was downloaded to all devices.
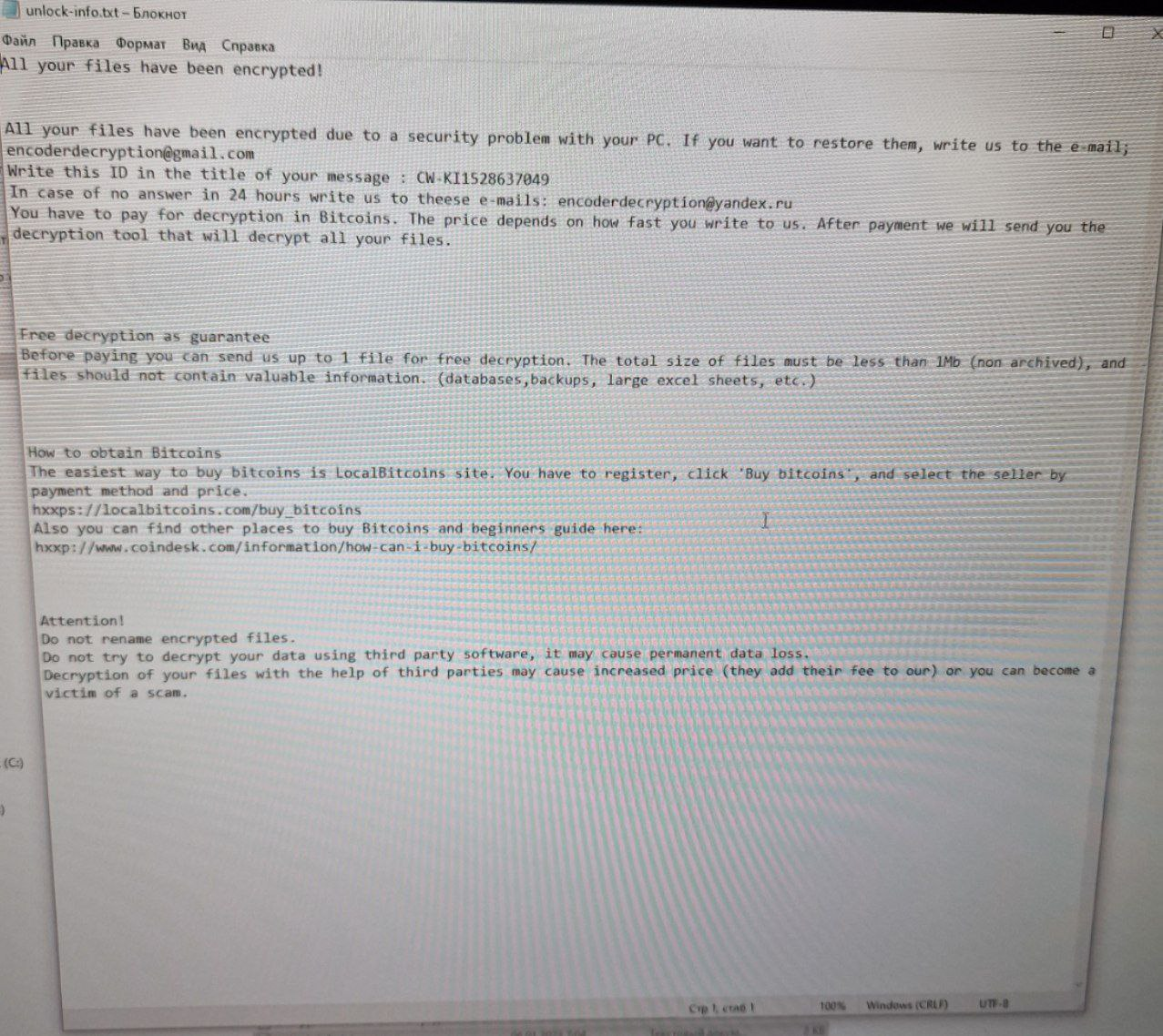
Encrypted files received the extension (CW-WL3048625917) and executed commands designed to stop various services and disable certain features in the Windows operating system, such as SQL Server, Virtual Disk Service, Volume Shadow Copy Service, and Windows Firewall. In addition, the ransomware copied itself to the startup folder: C:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartUp\, and created the unlock-info.txt file in the directories, a ransom note.
The analysis showed that the cyber attack was supposedly implemented in this way:
KZ-CERT staff made the following recommendations:
Information security incident prevention recommendations
- Connect to the Internet via Unified Gateway to Internet Access.
- Differentiate user rights according to the rules of the access control policy or according to UR.
- User accounts must have sufficient rights and privileges to perform daily tasks without the possibility of making modifications to the security policy, rights and privileges of other administrators.
- In accordance with clause 9.3.2 of the ST RK ISO/IEC 27002-2015 standard for managing privileged access rights, the distribution and use of privileged access rights should be limited and controlled.
- Install a licensed operating system for servers and workstations.
- Close access via the RDP protocol.
- Use licensed information protection tools.
- Periodically update operating systems and application software.
- Change passwords regularly and as needed.
- Set up event logging in the intrusion detection and prevention system.
Recommendations when observing signs of infection of a workstation with a ransomware virus, which will help keep some files from being encrypted.
- As soon as the first signs of ransomware infection appear, immediately turn off the power of the workstation.
- Prepare a boot disk along with anti-virus software.
- Scan the infected disk with anti-virus tools, quarantine the found viruses.
- Do not get in touch with intruders.
- Determine the type of encryptor and use third-party utilities to decrypt files.
- If third-party utilities did not help, but encrypted files are of critical value, it is worth sending samples of encrypted data and the body of the encryptor to specialists for manual analysis. At the same time, it is important not to remove the ransomware from quarantine or reinstall the OS, since the ransomware often uses unique OS identifiers or virus copies to generate keys.
Recommendations for reducing the damage caused by encryption and reducing the risk of infection of a workstation with a ransomware virus.
- Store a backup on a network storage.
- Set up automatic backup according to UR requirements.
- Install and regularly update anti-virus tools on workstations.
Recommendations for technical specialists on active search for IS threats.
- Check an events related to the creation of suspicious folders or files, or the launch of processes such as rundll32.exe or regsvr32.exe using winword.exe/excel.exe.
- Check for suspicious launches of cscript.exe / wscript.exe, especially those related to network activity.
- Scan powershell.exe processes with suspicious or obfuscated (disguised) command lines.
- Analyze executable files and scripts placed in the startup folder, added to the Run keys or launched using the task scheduler.
- Check the execution of sdbinst.exe for suspicious command line arguments.
- Check the creation of new keys in the HKLM\SOFTWARE\ Microsoft\Windows NT\CurrentVersion\Image File Execution Options section.
- Verify that security systems can detect prompts specific to credential dumping tools such as Mimikatz.
- Search for artifacts specific to network intelligence tools, such as AdFind command line arguments.
- Check and identify artifacts associated with the execution of files from unusual locations, such as %TEMP% or %AppData%.
- Detect registry and Windows firewall modifications related to RDP connections.
- Monitor and analyze connections over RDP to detect attempts to move through the network.
- Detect wmic.exe launches using suspicious requests.
- Verify that your systems can detect Cobalt Strike Beacon payloads and similar tools specific to post-operational frameworks (at least those launched with typical command line arguments and from typical locations).
- Track the creation events of new services related to PsExec, SMBExec and other dual purpose or penetration testing tools (pentest).
- Monitor executable files that are disguised as common system files (such as svchost.exe) but have anomalous parent files or locations.
- Watch for signs of unauthorized use of remote access tools on your network.
- Monitor cloud storage client installation events and cloud storage access events and check if they are legitimate.
- Monitor common FTP programs on end hosts for file installation events with malicious configurations.
KZ-CERT published materials on the official Internet resource – https://www.cert.gov.kz/news/13/2057 to minimize the risks of malware and ransomware attacks.