INFOSTEALER IS THE CAUSE OF PERSONAL DATA LEAKAGE OF KAZAKHSTANI CITIZENS
National Computer Incident Response Service KZ-CERT JSC “State Technical Service”, reports an increase in the number of information security incidents related to the leakage of personal data. The cause of leakage is infostealers, malicious software, which are aimed at stealing personal data (passwords, banking data and other sensitive information) from infected computers. This type of malware is designed to operate covertly and transmit stolen data to attackers.
Infostealers (or information Trojans) are a type of malicious software designed to collect sensitive data from a victim’s PC. They steal personal data such as accounts, passwords, credit card numbers and other sensitive information. There is a subspecies of infostealers, keyloggers, which log user keystrokes. They, too, are designed to collect sensitive user information
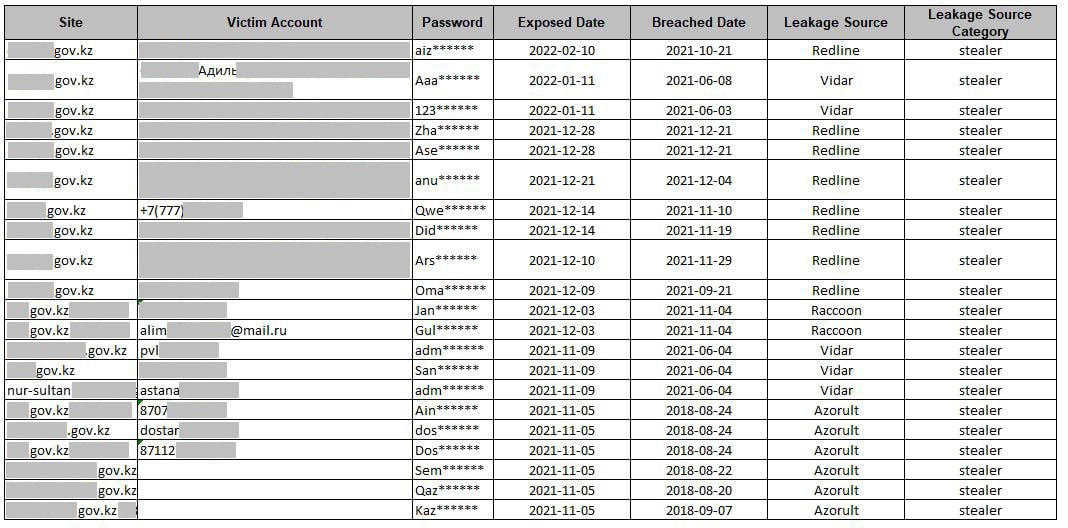
During the analysis of information security incidents, KZ-CERT experts identified infostealers that were the cause of personal data leakage:
- ReadLine Stealer – sold on closed forums and used by attackers to steal data and download other viruses to the victim’s device. It can steal logins, passwords, autofill data, cookies and credit card data, from all web browsers. Hackers can misuse this information to access various accounts (e.g. social media, email, bank accounts, cryptocurrency wallets).
- Vidar Stealer is an infostealer that is capable of stealing and transmitting sensitive data from the victim’s computer, including banking information, stored passwords, IP addresses, browser history, login credentials and cryptocurrency wallets to the attacker’s server. Vidar Stealer is distributed via spam emails, pirated software, key generators, etc.
- Raccoon Stealer – designed to steal data from PCs and systems. It is a typical member of the infostealer category that aims to collect sensitive information such as account logins and passwords, bank card details and other personal information. It spreads in a variety of ways, including malicious email attachments, compromised websites, or through exploits in software. Typically, their goal is to stealthily infiltrate target systems to collect information without attracting attention.
- Azorult Stealer – Often used to collect data such as logins, passwords, bank card details, browser cookie information and other valuable information. Can be spread via malicious emails, malicious websites, compromised software or exploits. Once infected, it collects information, which it then sends to a remote server controlled by the attackers.
When it comes to personal data leakage due to an infostealer, it more often means that a major information security breach has occurred. Usually, such situations require serious investigation and measures to prevent similar incidents in the future.
So how can you realize that your PC has fallen into the “crosshairs” of a hacker? For example, in terms of detecting the possible presence of Redline Stealer software, look for the following signs:
– Pay attention to increased RAM usage, which may indicate the presence of a malicious software.
– Use network activity monitoring tools, such as Task Manager in Windows, to monitor processes communicating with the Internet. address any suspicious connections.
– check the Appdata folder for suspicious executables, as malware often uses this directory to hide.
– use general system monitoring to detect unusual or suspicious activity, such as running unfamiliar processes.
To ensure cybersecurity and minimize the risks of your personal data being leaked, it is worth paying attention to some recommendations:
- Check your personal computer with an antivirus. You can scan with antivirus scanners (KVRT, Dr.Web Cure It).
- Make sure that your computer has up-to-date antivirus software and regularly update its database.
- Do not install pirated software and download only from official resources of software companies.
- Check the external drive that you have used before for viruses using anti-virus software (because often software is located there and after removing the drive a new scan of the anti-virus shows that no malicious objects are detected).
- Set up two-factor authentication (2FA) for your online accounts to enhance security and prevent unauthorized access.
- When using electronic digital signatures, we recommend you to use secure media such as Kaztoken, eToken, SafeNet eToken 5100\5105, or use cloud EDS, mobile EDS, recommended for use by the National Certification Centre of the Republic of Kazakhstan.
- Do not click on links in emails or websites that you consider suspicious or unreliable. Phishing attacks can use fake links to steal data.
These recommendations will help strengthen digital security and prevent infostealer threats. Cybersecurity is becoming an increasingly important aspect of any company, so it is essential to continuously improve methods of defense against cyber threats, including the prevention of spies, both real and digital.