DARKTORTILLA EXPOSÉ: CYBER THREAT TO PERSONAL DATA OF KAZAKHSTANI CITIZENS
In September of this year, in order to analyze and further eliminate the IS incident in the networks of government agencies, the National Computer Incident Response Service of the State Technical Service JSC (KZ-CERT Service) received information from a Kazakhstani company about a file with Agent Tesla and DarkTortilla, which together represent an infostealer.
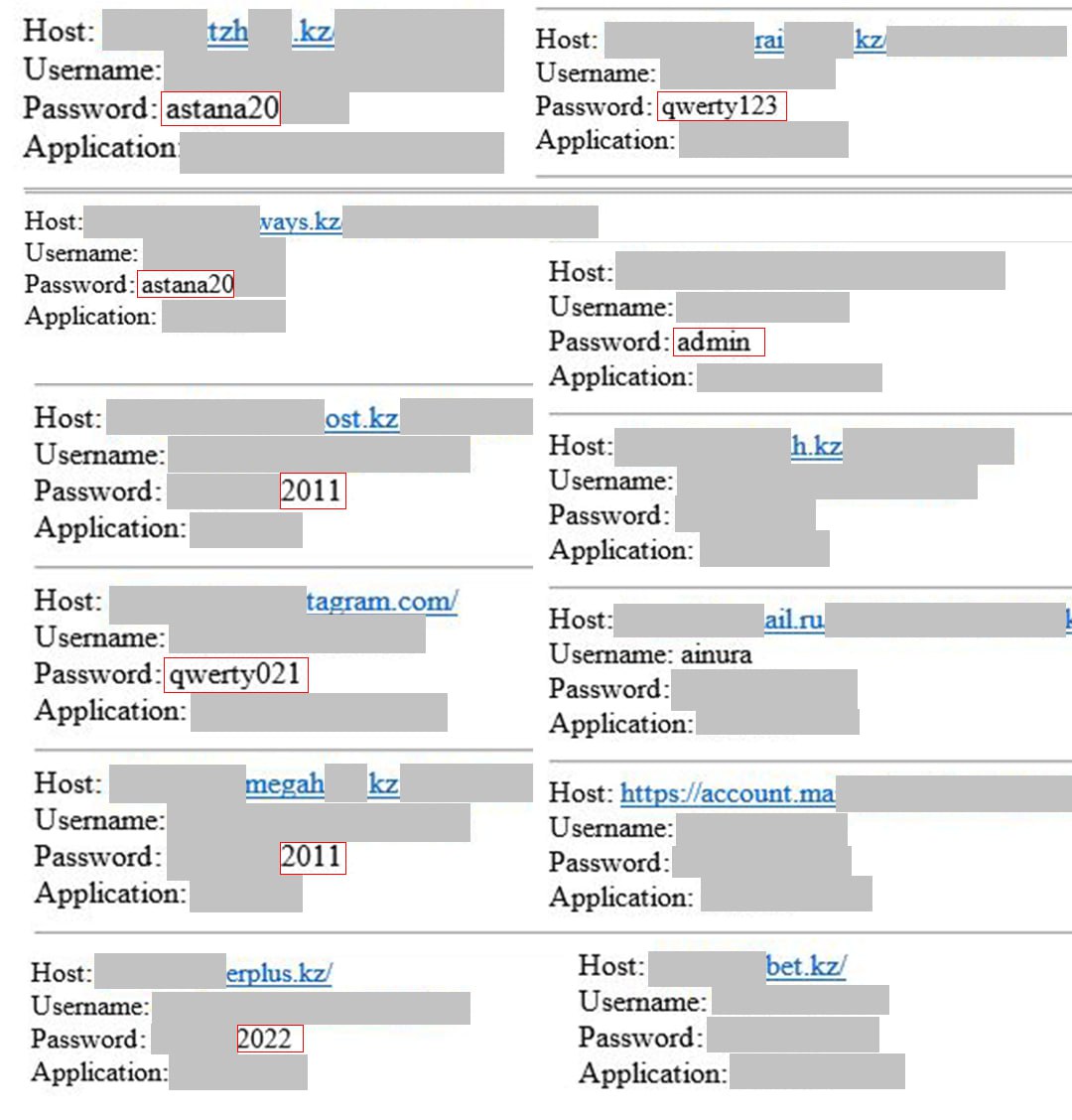
According to the company’s information, the file, in which the e-mail addresses of Kazakhstani citizens were found (Figure 1), was used by hackers for spying purposes.
Specialists of KZ CERT Service analyzed the received file and recreated the algorithm of actions of infostealer. Thus, it turned out that the attacker sent the file to the user, and after opening the file, the infostealer was launched, which collected confidential information from the computer, including website addresses with logins and passwords. In parallel, the infostealer took screenshots every 20 minutes and tracked users’ keystrokes according to the attacker’s prescribed requests.
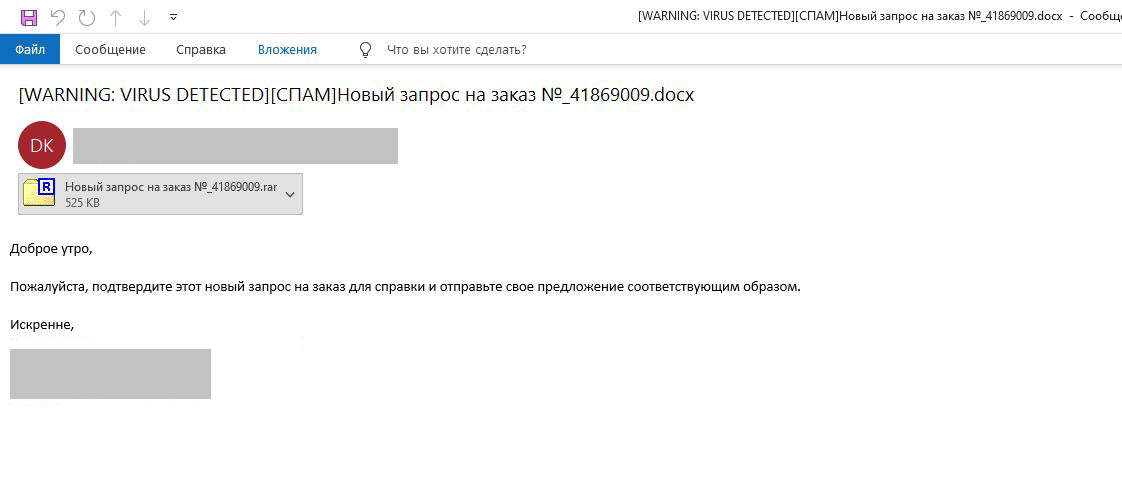
After receiving the detected sample, the file name: “New Order Request #_41869009.exe” and the original name: oasaesasaaaaa.exe became known (Fig 2).
AGENT TESLA and DARKTORTILLA
In the world of cybercrime, the number of tools that hackers use is increasing every day. In this case, we will reveal the tactics of one of the most sophisticated cyber threats of our time – DarkTortilla.
Here’s a bit of background on DarkTortilla. It is a versatile tool for cybercriminals, it is based on .NET and has settings associated with the RATs Crew. In addition, there may be similarities to the Gameloader malware.
Agent Tesla, which was used in conjunction with DarkTortilla, is an infostealer capable of stealing personal data from web browsers, email clients and FTP servers: passwords, keys and other sensitive data. The latest versions of Agent Tesla are also capable of mining personal data from VPN clients.
Fig. 3
CODE ANALYSIS AND IMPORTANT FEATURES OF DARKTORTILLA
DarkTortilla uses the steganography method to hide its configuration. In this case, the sample configuration is stored in 14 files (images).
*Steganography is the technique of hiding information within images or other media files so that this information remains invisible to normal visual analysis.
DarkTortilla uses an anti-analysis technique to bypass attempts to analyse and detect malicious code. More specifically, it checks the equality of the file name with “ystem32” and the current folder with “scan”. If both of these conditions are valid, the execution of the programme is prematurely terminated. This mechanism represents part of DarkTortilla’s obfuscation and self-protection. Detection of “system32” and “scan” may indicate an attempt to analyze or dynamically decompile the code. If these conditions are detected, the malware stops working, making it difficult to analyze and investigate. This is one of the ways DarkTortilla ensures its persistence and “hiding” in the system.
DarkTortilla copies itself to the %appdata%\\random_name\\random_name folder after infecting the system.
This is one of the tactics that malware can use to ensure a long-term stay on the system.
DarkTortilla uses the Qb63() function with the XOR algorithm to decrypt the payload.
PAYLOADS
In the next step, DarkTortilla presents the decrypted payload. It checks for network availability using the InternetGetConnectedState function and, if no network is available, terminates execution. The sample also obtains the IP address of the current computer using the api[.]ipify[.]org service.
The infostealer also includes keylogger functionality to track keystrokes using the SetWindowsHookEx() function. Its main task is to exfiltrate sensitive data such as passwords, keys and settings of user programs including browsers, email clients, VPN and FTP clients and more. Moreover, the sample regularly creates screenshots of the screen using Graphics.CopyFromScreen() at 20-minute intervals.
DATA EXFILTRATION
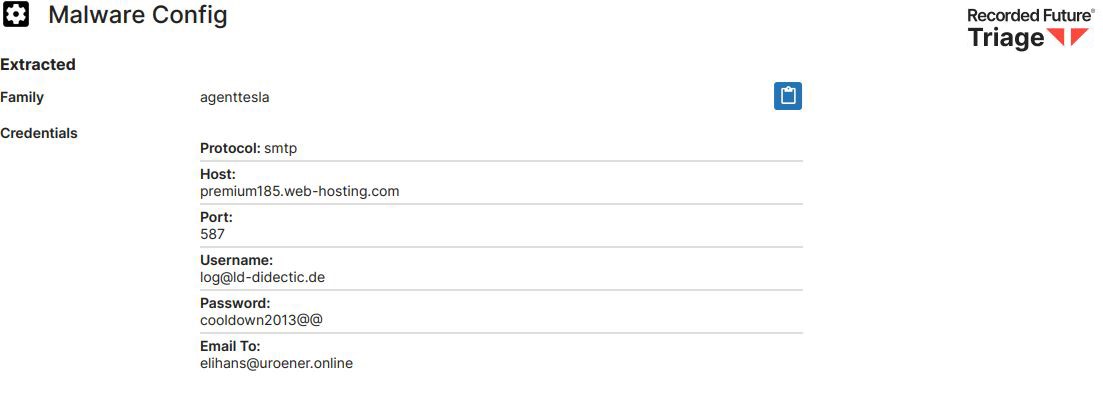
All collected sensitive data is transmitted using the SMTP protocol. An email is generated with “elihans@uroener.online” as the sender and “log@ld-didectic.de” as the recipient. The password used to access the account is: cooldown2013@@@. The mail server used for sending is: premium185.web-hosting.com. The email is sent as an HTML attachment with a name in the format yyyy_MM_dd_HHH_mm_ss.html.
MAIN FUNCTIONALITY
The main tasks of DarkTortilla are collecting sensitive data from user programs, keylogging, system profiling and creating screenshots of the screen. This multifaceted tool is capable of remaining invisible in the system, as well as continuously collecting and transmitting sensitive data to cybercriminals.
Based on the analysis, KZ CERT Service specialists report that DarkTortilla and its related software Agent Tesla pose a serious threat to the security of data and personal information.
KZ CERT has sent cyber hygiene recommendations and notices to Kazakhstani users who were attacked.
We strongly recommend using complex passwords and not opening suspicious files, as well as taking general cyber security measures to protect your systems from similar cyber threats.
If you have experienced an information security incident, please report it to us on the toll-free number 1400 (24 hours a day), via telegram bot @KZ_CERT_chat_bot or email: incident@cert.gov.kz.