Kazakhstani users do not renew SSL/TLS certificates
JSC “State Technical Service” reports that in the course of the study of the National Top Level Domains .KZ by the National Computer Incident Response Service KZ-CERT, a number of certificate-related problems were identified on various Internet resources. The research was conducted on over 170,000 Internet resources to assess the quality of their SSL/TLS certificates (registration certificates). This is an important aspect of information security, as SSL/TLS certificates are used to ensure secure communication between clients and servers.
The detected problems may affect the security and protection of user data on these Internet resources. The study highlights problems not only with SSL/TLS certificates, but also with the cipher suites used on the Internet resource. Examples of such problems may include outdated or invalid certificates, incorrect encryption settings or insufficient use of modern cryptographic protocols.
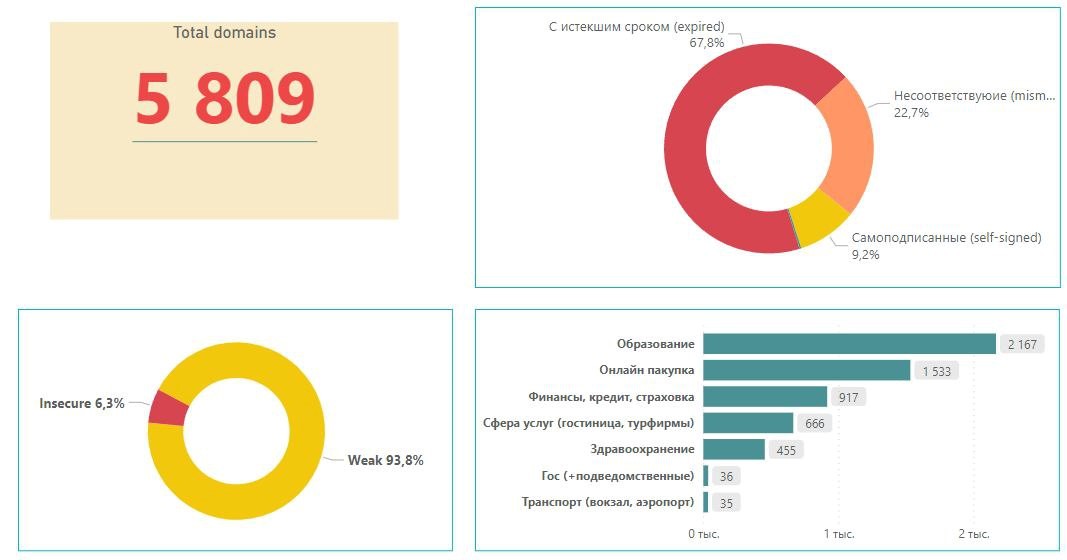
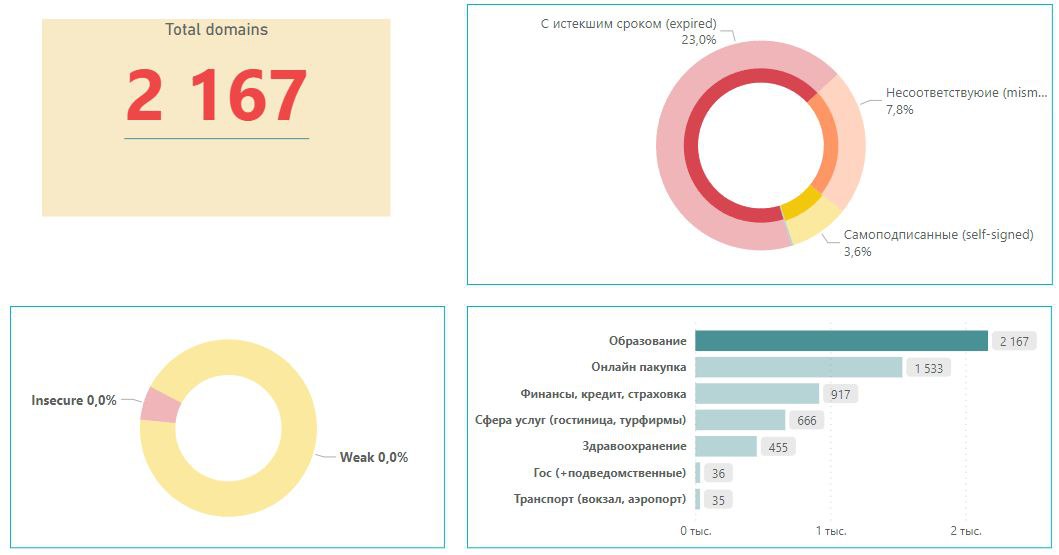
KZ-CERT specialists have identified more than 126,000 Internet resources as having potential information security problems. To date, they have identified 5,809, 38% of which are in the education sector, of which 8% have an expired SSL certificate.
pic 1
pic 2
The analysis reveals that some servers, use RSA algorithm with keys longer than 3072 bits. They may encounter performance issues while authenticating. This can lead to connection delays and even unavailability of the service with a large number of users.
Technical problems using RSA keys can also occur with Advanced Encryption Standard (AES) encryption using Cipher Block Chaining (CBC) mode, especially in versions of TLS 1.0, SSL 3.0 and below. CBC mode is also vulnerable to plaintext attacks. Galois/Counter Mode (GCM) is recommended for enhanced security.
The Triple-DES algorithm (3DES EDE CBC) has become vulnerable in the past and is considered obsolete. Standardisation projects are increasingly abandoning its use due to the risks and vulnerabilities associated with the CBC mode.
RC4 128 encryption is also considered obsolete and insecure due to identified vulnerabilities and is therefore prohibited for use in TLS protocols.
HMAC SHA-1 is also considered outdated and vulnerable because it has been demonstrated that it is possible to create two different datasets with the same SHA-1 hash. It is recommended to use more modern versions of hash functions such as SHA-256 or SHA-3 to ensure data security.
Outdated security methods can expose users to the risk of hacking. Attackers can exploit vulnerabilities in these methods to gain access to sensitive information. Some of these legacy methods are easily cracked, increasing the likelihood of unauthorized access to information. If encryption keys are “leaked”, attackers can decrypt large amounts of information. This could result in identity theft or financial loss to users.
For recommendations and detailed information on analyzing certificate information for Internet resources located in other domain zones, please refer to the recommendations section of the CERT.GOV.KZ website